0ops 0CTF 2017
· 阅读需 2 分钟
探索 http://www.0ops.net/cli.html
可用命令
help
ls
co
cat
whoami
clear
whosyourdaddy
sudo
wget
curl
hint
konami.
第一次 大力出奇迹
比较懒,直接审查元素,找到了相关的js 0ops_cli_all.js
美化了一下js http://tool.lu/js/
然后大致看了一下,发现了这个
window["\x65\x76\x61\x6c"](Terminal["\x72\x75\x6e\x43\x6f\x6d\x6d\x61\x6e\x64"](unescape("%63%75\x72%6c%20%66%6c\x61%67%5f\u0069%73%5f%6e\x6f%74\u005f\u0068%65%72%65")))
即
window["eval"](Terminal["runCommand"](unescape("%63%75r%6c%20%66%6ca%67%5f\u0069%73%5f%6eo%74\u005f\u0068%65%72%65")))
> unescape("%63%75r%6c%20%66%6ca%67%5f\u0069%73%5f%6eo%74\u005f\u0068%65%72%65")
< "curl flag_is_not_here"
运行 以上命令得
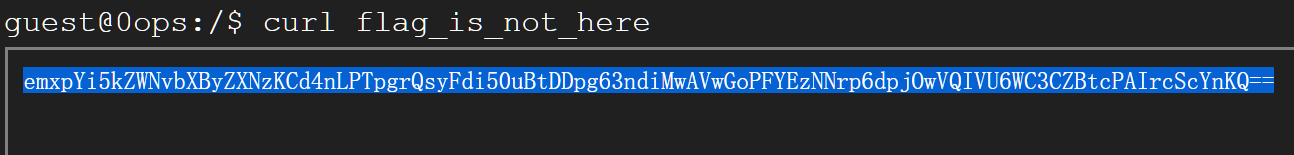
emxpYi5kZWNvbXByZXNzKCd4nLPTpgrQsyFdi50uBtDDpg63ndiMwAVwGoPFYEzNNrp6dpjOwVQIVU6WC3CZBtcPAIrcScYnKQ==
用Python解得
>>> import base64
>>> base64.b64decode("emxpYi5kZWNvbXByZXNzKCd4nLPTpgrQsyFdi50uBtDDpg63ndiMwAVwGoPFYEzNNrp6dpjOwVQIVU6WC3CZBtcPAIrcScYnKQ==")
"zlib.decompress('x\x9c\xb3\xd3\xa6\n\xd0\xb3!]\x8b\x9d.\x06\xd0\xc3\xa6\x0e\xb7\x9d\xd8\x8c\xc0\x05p\x1a\x83\xc5`L\xcd6\xbazv\x98\xce\xc1T\x08UN\x96\x0bp\x99\x06\xd7\x0f\x00\x8a\xdcI\xc6')"
>>> import zlib
>>> zlib.decompress('x\x9c\xb3\xd3\xa6\n\xd0\xb3!]\x8b\x9d.\x06\xd0\xc3\xa6\x0e\xb7\x9d\xd8\x8c\xc0\x05p\x1a\x83\xc5`L\xcd6\xbazv\x98\xce\xc1T\x08UN\x96\x0bp\x99\x06\xd7\x0f\x00\x8a\xdcI\xc6')
'>++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++.<+++++++++++++++++++++++++++++++++++++++++++++++++.>------------------.+++++++++++++++++++.++++++++++++++++++++++++.<.>------------------------------------------.++++++++++++++++++++++++++++++++++++++++++.-----------------.<-.>++++++.+++++++++++.-----------------------.---------------------.+++++++++++++++++++++++++++++++.-------------------------------.'
目测某fuck语言 Brainfuck
web解释器El Brainfuck
得到真正的Flag
F14G_15_N0T_H3R3
第二次 常规方法
Hint:
guest@0ops:/$ hint
________________________________________________
< Do you know konami, konami, konami and konami? >
------------------------------------------------
\ ^__^
\ (xx)\_______
(__)\ )\/\
U ||----w |
|| ||
guest@0ops:/$
在找到 hint 后,搜索一下就可知: konami指的是一组热键 ↑↑↓↓←→←→BA —— Konami Code - Wikipedia
尝试一下
ori
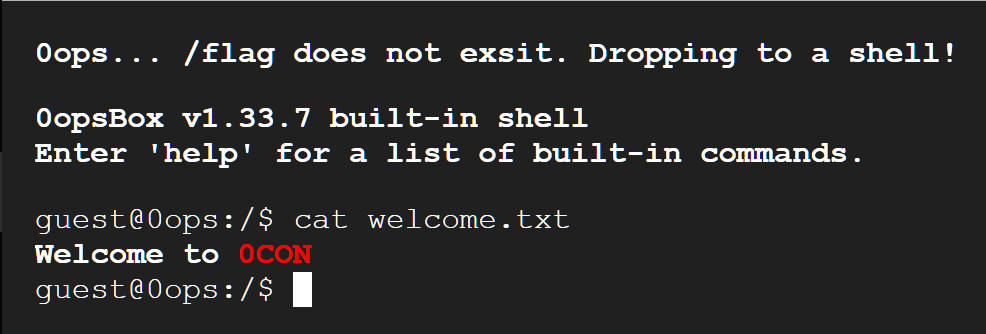 1st
1st
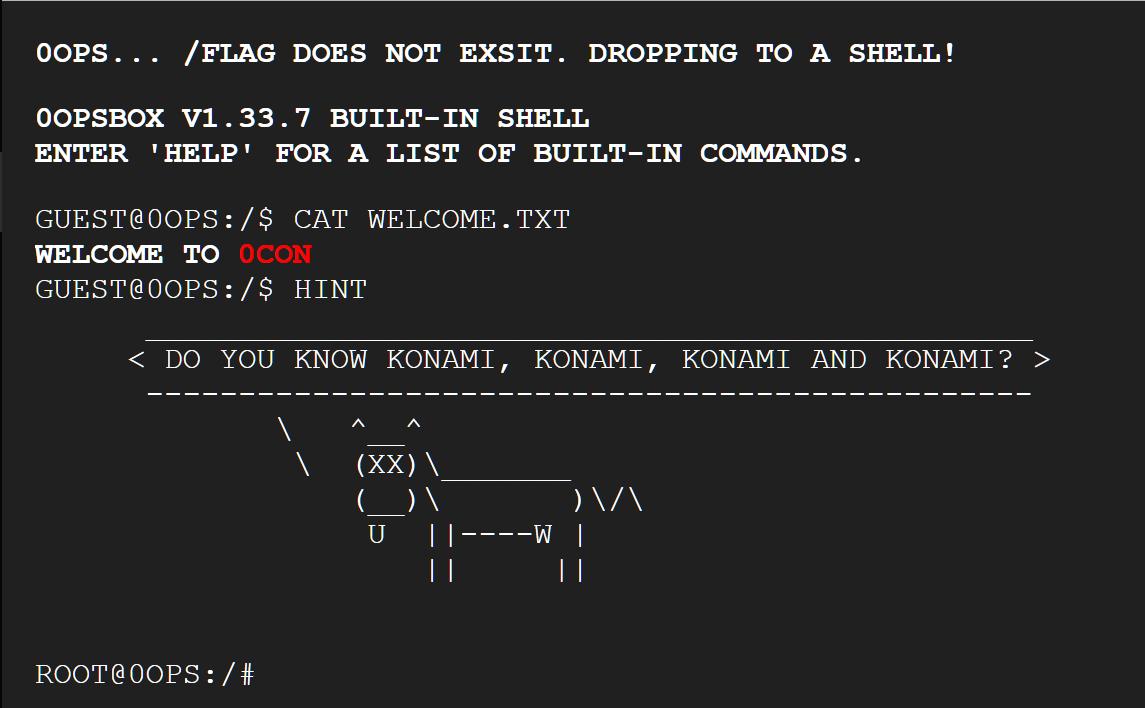 2nd
2nd
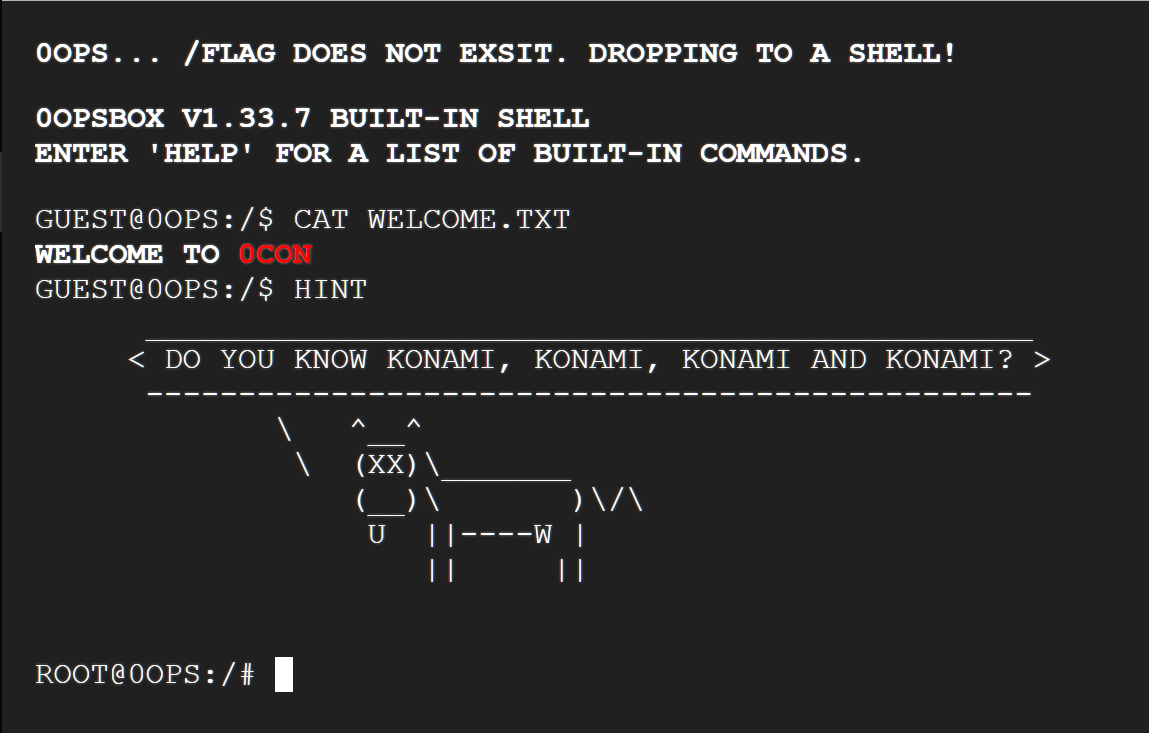 3rd
3rd
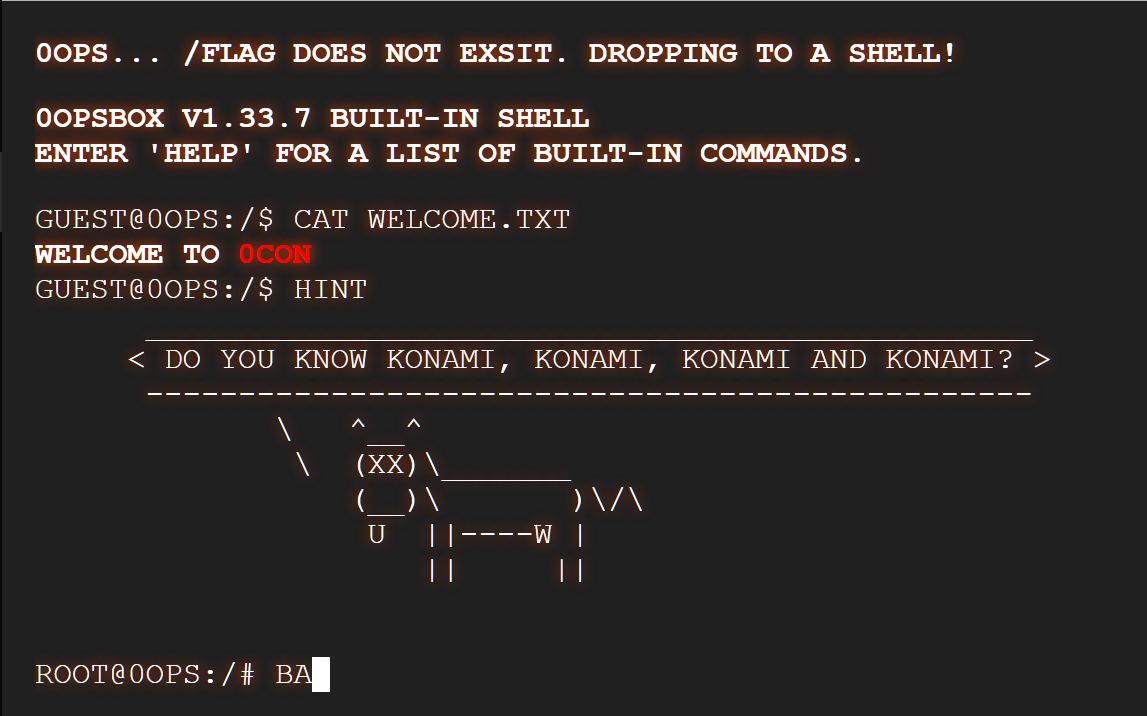 4th
4th
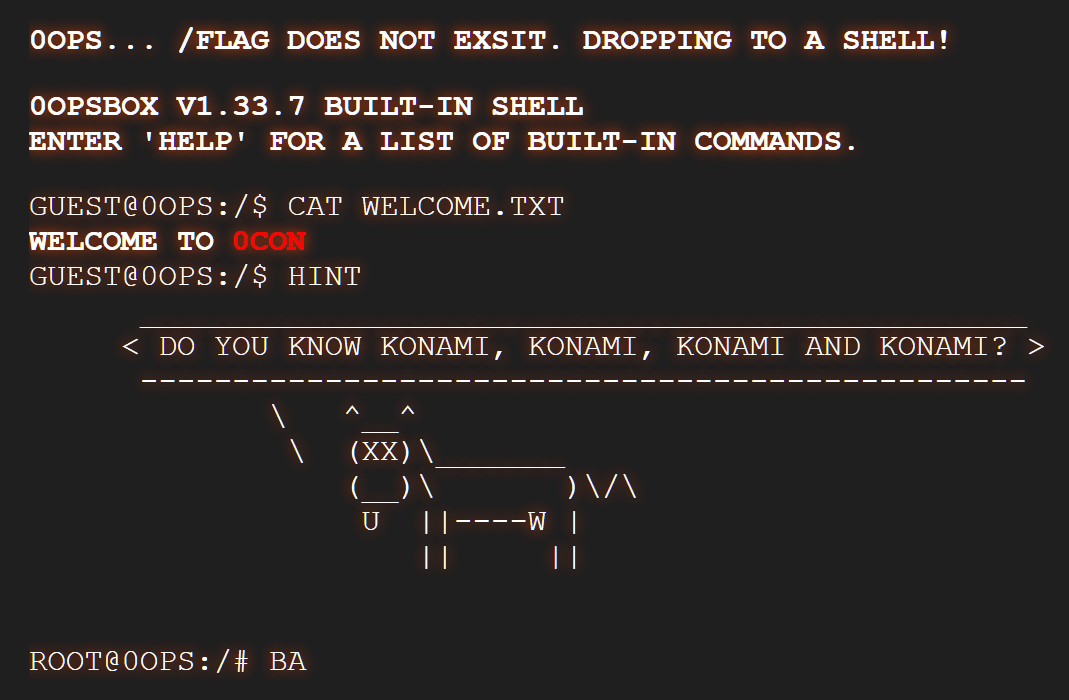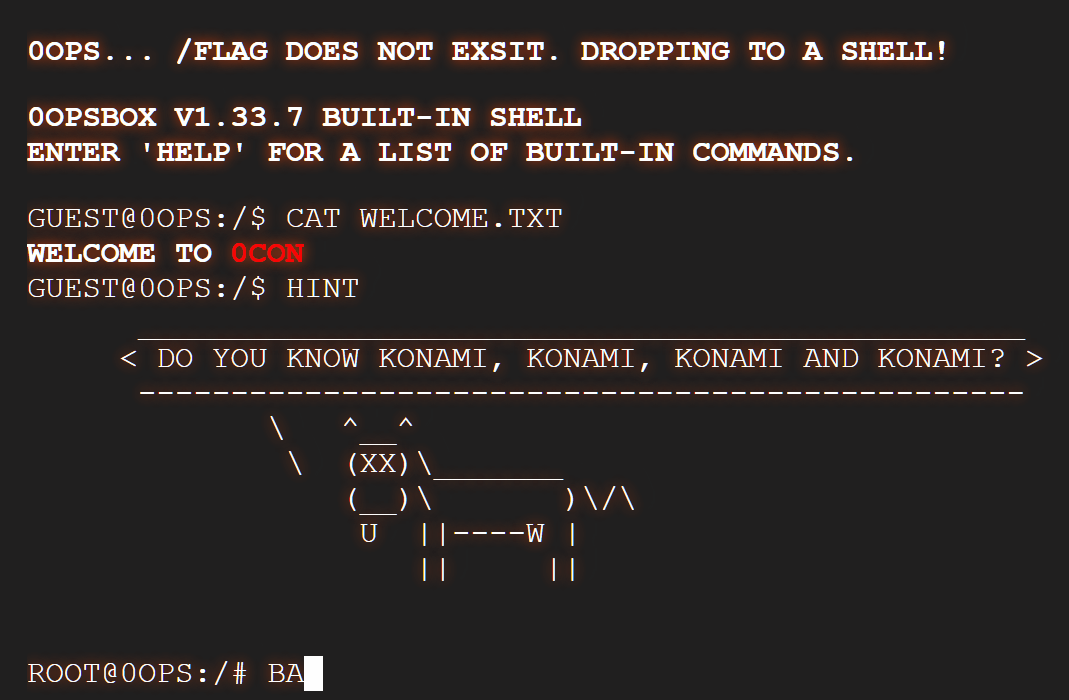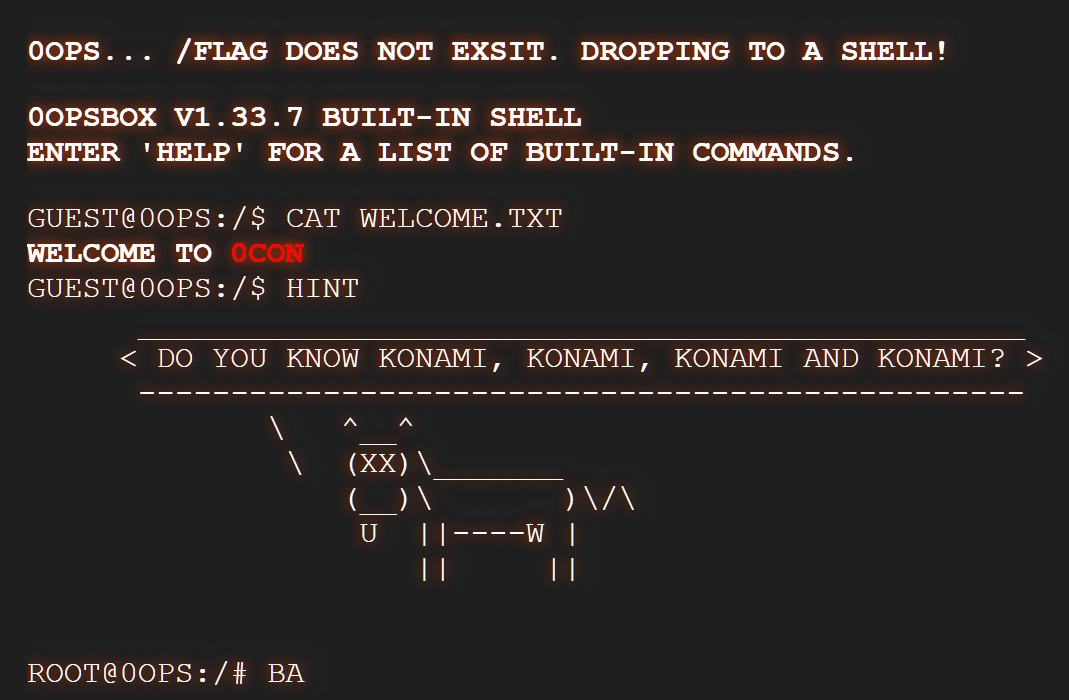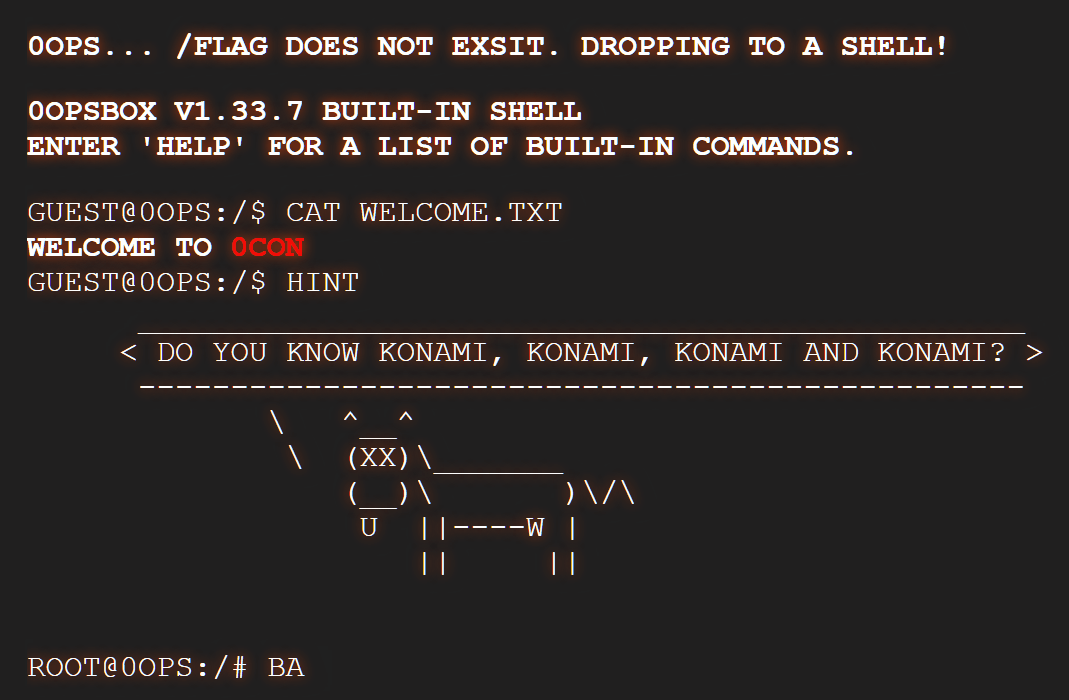 result
result
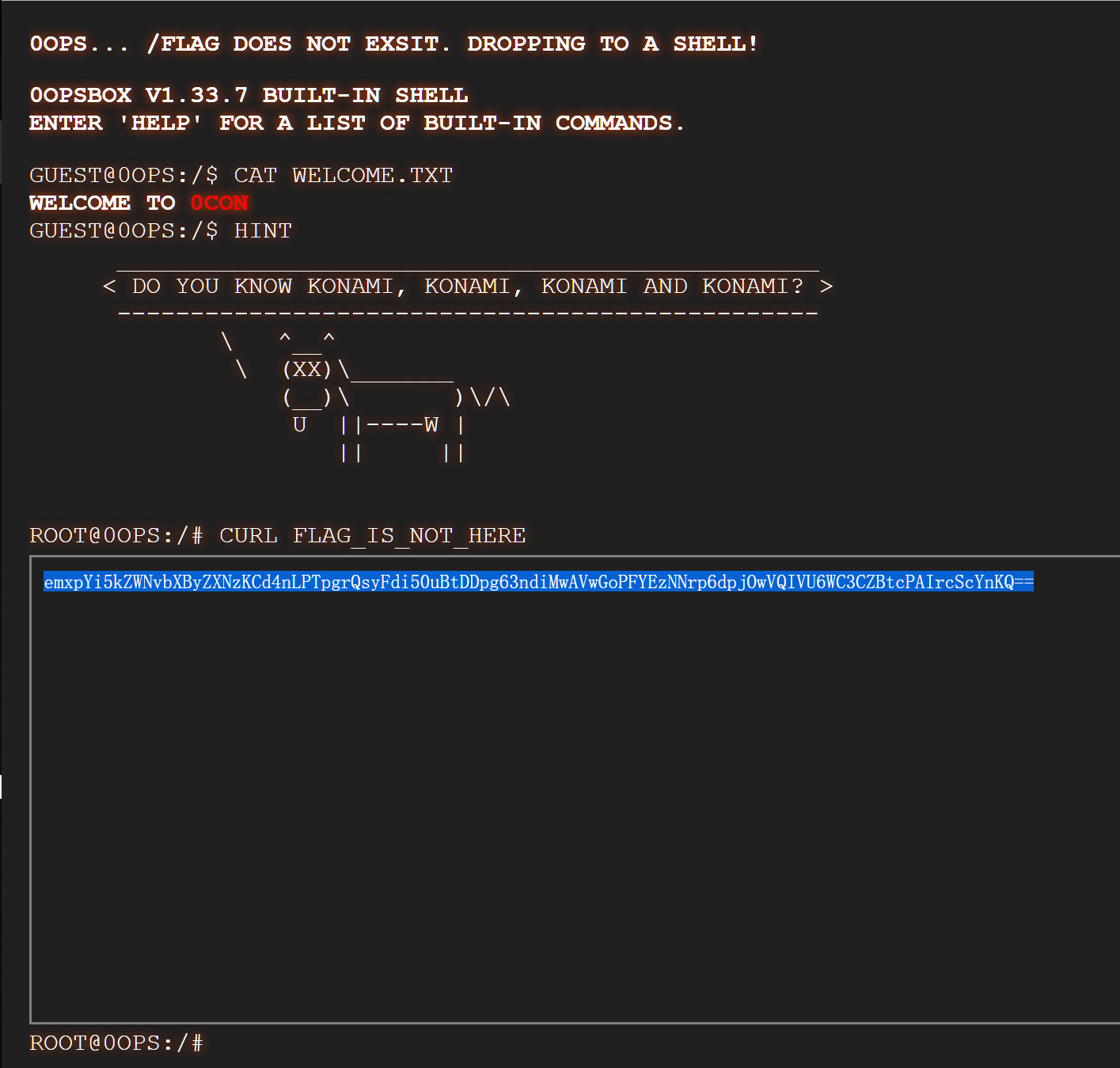
接下来的解密同上
